
Determine Who Your Beneficiary Is Without Invading Privacy
Why Do VASPs Need to Know Who Their Beneficiary Is?
Prior to the Travel Rule, identifying the beneficiary and the beneficiary’s VASP was not required. With its implementation, the Travel Rule requires virtual asset service providers (VASPs) to know where funds are being sent, to whose self-hosted wallet address, to which VASP, and to whom the account belongs; this is to verify the legitimacy of transactions to prevent illicit money flows.
This prerequisite poses quite a challenge to the originator VASP. How do they get this information? Yes, the originator customer can be asked, but can the VASP truly rely on the customer’s information, especially regarding compliance?
A VASP’s main goal is to conduct transfers quickly and cost-efficiently while remaining compliant with the Travel Rule—not just for their customers but also for their business. Therefore, utmost care needs to be taken when complying with the Travel Rule, and this is to be done through a technological means.
How Can VASPs Determine Who The Transaction’s Beneficiary Is?
VASPs can determine who their beneficiaries are via several methods; however, this text will focus on 2 methods: the “network discovery” method and the “Travel Address.” Each method has pros and cons, although the Travel Address is the ideal method for complying with data protection laws and protecting the privacy of the address holder.
The Network Discovery Method: How Does It Work?
With the network discovery method, Travel Rule solution providers can disclose the owner of an address upon request, introducing a new layer of transparency.
The originator customer will notify its VASP, the originator VASP (VASP O), that they wish to send assets to a specific address. VASP O submits the said address to the Travel Rule Solution provider’s database, where it is hashed and searched for against existing hashed addresses. If a match is found, the Travel Rule solution provider can disclose the owner of that address to the originator VASP.
The Network Discovery Method: Pros and Cons
This method promises to offer real-time identification of the counterparty. Additionally, when a transaction is initiated to an address, the database retrieves and confirms which VASP owns the hashed address, facilitating seamless transactions within the network.
On the other hand, this practice poses severe business confidentiality concerns as the solution providers—or middlemen—gain insight into the business activities of various VASPs, potentially enabling industrial espionage. This approach raises its own set of privacy and security challenges, such as the risk of data breaches and unauthorised access to personally identifiable information (PII).
What’s more, as VASPs have not conducted their own due diligence, as requested by the EU’s Transfer of Funds Regulation (TFR) and the FATF, there is the added risk of sending PII to an untrustworthy VASP. This method can also allow companies to research their competitors or even mine data, as in the case of blockchain analytics companies.
Both VASPs do not communicate with each other, but the Travel Rule Solution provider acts as an intermediary or rendezvous point between them. This process exposes a privacy loophole: once the Travel Rule Solution Provider identifies the address corresponding to the hash, the privacy scheme becomes compromised, serving more as a facade than a robust protection measure. In addition, what happens if the hashed address does not exist within the cloud-based database?
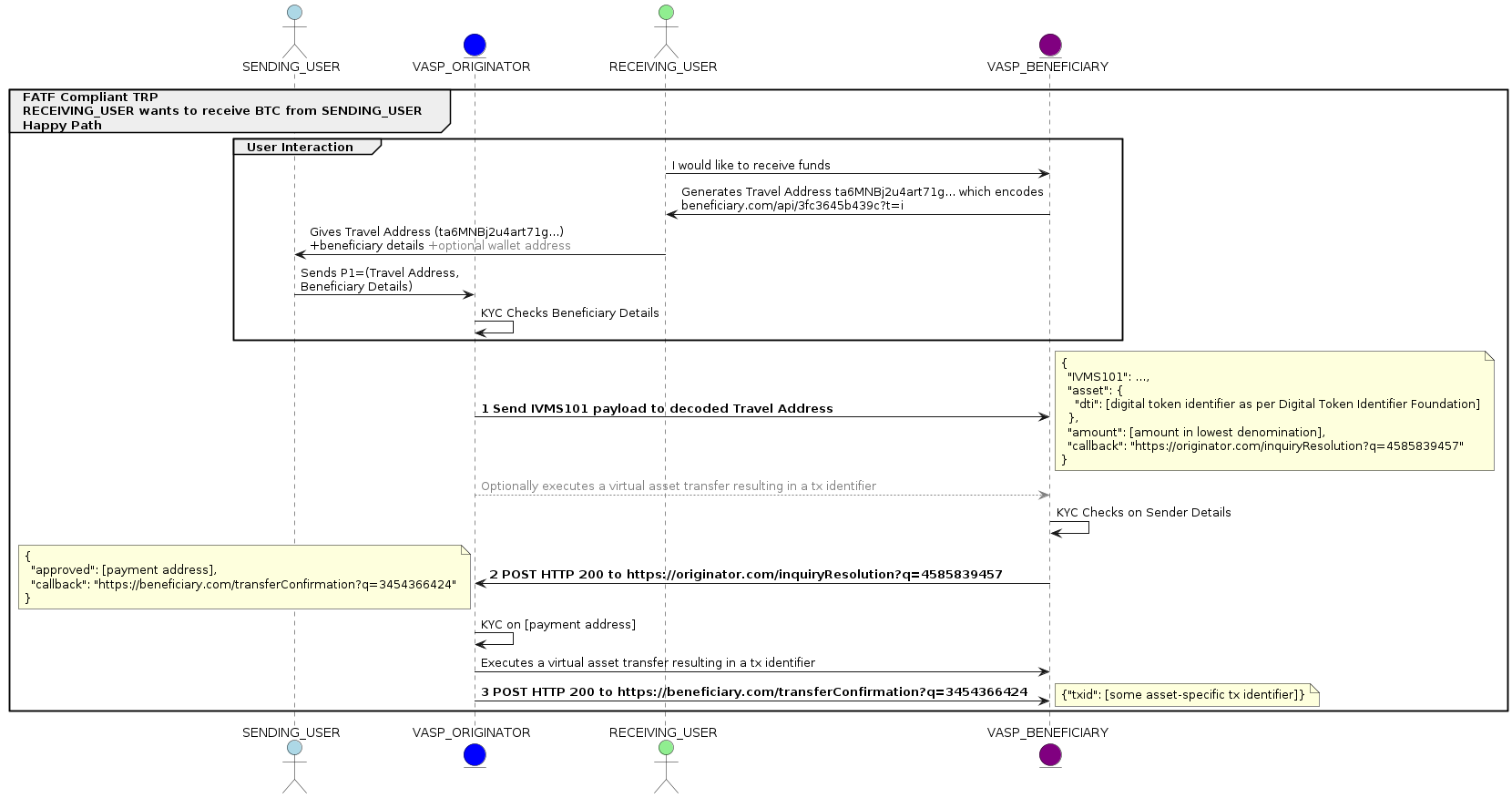
The Travel Address: How Does It Work?
Similar to a Bitcoin address, a Travel Address looks like a string of characters, but it identifies the VASP that controls the receiving address.
The beneficiary communicates their wish to receive crypto assets to their VASP, which generates a Travel Address (TA) for them. The beneficiary shares this TA with the originator, similar to how a beneficiary shares his bank account details with the originator in traditional finance. The originator provides the TA to their VASP along with the beneficiary’s details.
Behind the scenes, the originator's VASP conducts sanctions and politically exposed person (PEP) checks on the beneficiary, with the beneficiary's VASP performing similar checks on the originator. If satisfactory, the beneficiary's VASP transmits an address to the originator's VASP, and the transaction proceeds compliant with the Travel Rule. Finally, the Transaction ID is relayed to the beneficiary's VASP, completing the transfer process.
The Travel Address: Pros and Cons
With the Travel Address, VASPs can clarify where the crypto assets will be sent. Moreover, VASPs can verify if the beneficiary VASP has undergone KYV procedures before disclosing additional information and ensure that VASP B hasn't been subjected to sanctions, all important aspects of Travel Rule compliance. Using these outcomes, the VASP can determine how to proceed with the transaction, preventing non-compliant transactions.
Regardless of who receives a Travel Address, the end user will not be able to use the address unless they have access to a Travel Rule solution that has implemented Travel Rule Protocol (TRP), and even then, it is one of the safest identifiers currently available because the Travel Address as no personal information is disclosed when sharing a Travel Address.
One drawback is the Travel Address is unique to the TRP; therefore, only counterparties who use a Travel Rule solution with TRP as one of its protocols can enjoy this functionality.
But, the same can be said for network discovery methods—if the user does not use the relevant Travel Rule software, they, too, will not be able to use the functionality.
What Next: How Should VASPs Proceed?
Complying with the somewhat conflicting requirements of data protection and anti-money laundering data exchange is a big challenge for VASPs. While network discovery offers real-time identification, it raises significant privacy concerns due to middleman involvement and the potential for data breaches.
The Travel Address provides a safer option, as it is point-to-point (no middleman is involved), so VASPs can confirm transaction details without compromising personal information; as no intermediary service is involved, there is less chance of failure and outside prying.
Moreover, by conducting thorough KYV procedures and adhering to Travel Rule compliance standards, VASPs can ensure the security of transactions while protecting privacy.



